Compliance and risk management tools






Want to implement tools for anonymization and/or retention of personal data?
Make an appointment
Ensuring regulatory compliance continuously, instead of reacting periodically to non-conformities revealed during audits or gap analyses.
Making informed decisions based on real data, not declarations collected from interviews — supported by a verifiable audit trail.
Taking a proactive and preventive approach to threats and vulnerabilities, instead of responding only after security incidents or data breaches occur.
Conducting systematic risk assessments based on current, factual data, rather than periodic snapshots from audit reports.
Building awareness and engagement among employees in information protection, instead of adding more unused IT tools.
Acting consistently based on defined processes, rather than irregular activities triggered only during crisis situations.
Compliance requirements:
Why do we implement cybersecurity regulations such as NIS2, DORA, GDPR?
Does the organization remove all data for which the legal basis for processing has expired?
Business and operational requirements:
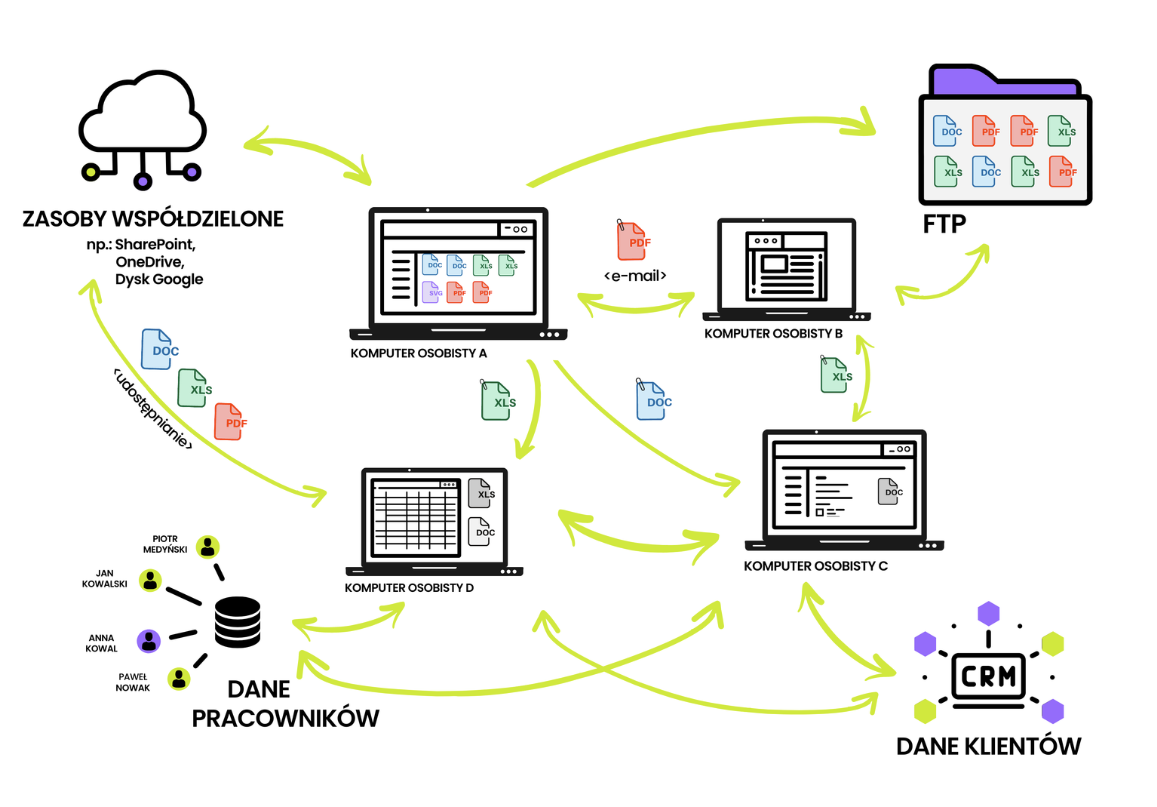
Where is critical information stored — including
personal data essential to the organization?
How can full data visibility be ensured across the entire organization?
Technical requirements for product development:
Are data in non-production environments properly anonymized?
How can we reduce the risk of data leakage during development and testing?
Compliance requirements:
 Safeguards ensuring compliance with NIS2, DORA, GDPR, ISMS ISO 27001
Safeguards ensuring compliance with NIS2, DORA, GDPR, ISMS ISO 27001
 Effective mitigation of information security risks and personal data protection risks
Effective mitigation of information security risks and personal data protection risks
Business and operational requirements:
 Support in mitigating negative impacts and ensuring timely, correct reporting of cybersecurity incidents
and personal data breaches, as well as executing data subject rights (access or deletion requests)
Support in mitigating negative impacts and ensuring timely, correct reporting of cybersecurity incidents
and personal data breaches, as well as executing data subject rights (access or deletion requests)
 Support in handling internal, supervisory, and certification audits under ISO 27001,
regulatory assessments, compliance checks, and inspections by the Data Protection Authority
Support in handling internal, supervisory, and certification audits under ISO 27001,
regulatory assessments, compliance checks, and inspections by the Data Protection Authority
 Support in fulfilling third-party requirements (clients and partners across the supply chain)
Support in fulfilling third-party requirements (clients and partners across the supply chain)
 Support in improving safeguards and risk-mitigation controls within the ISMS framework
Support in improving safeguards and risk-mitigation controls within the ISMS framework
Technical requirements of product development:
 Efficient preparation of synthetic business and personal data with production-like characteristics
for product development and testing, including AI solutions
Efficient preparation of synthetic business and personal data with production-like characteristics
for product development and testing, including AI solutions

Consequences of non-compliance:
 Violation of requirements under NIS2, DORA, GDPR.
Violation of requirements under NIS2, DORA, GDPR.
 Legal consequences imposed by regulators (e.g., the Data Protection Authority), including financial penalties,
temporary or full restrictions on data processing, or suspension of processes
(a ban on processing).
Legal consequences imposed by regulators (e.g., the Data Protection Authority), including financial penalties,
temporary or full restrictions on data processing, or suspension of processes
(a ban on processing).
 Personal liability of board members or management, including potential bans on holding executive functions.
Personal liability of board members or management, including potential bans on holding executive functions.
Business and operational consequences:
 Loss of reputation and trust of customers and partners.
Loss of reputation and trust of customers and partners.
 Loss of business following public disclosure of an incident or data breach.
Loss of business following public disclosure of an incident or data breach.
 Costly, ineffective manual data deletion processes carried out by personnel,
generating errors (e.g., excessive deletion) and data integrity incidents.
Costly, ineffective manual data deletion processes carried out by personnel,
generating errors (e.g., excessive deletion) and data integrity incidents.
 Barriers and blockers to effective and secure product development and testing —
including systems, applications, and AI solutions.
Barriers and blockers to effective and secure product development and testing —
including systems, applications, and AI solutions.

19.12.2025

15.09.2025

29.07.2025